Kerberos Authentication on Proxy Fails for One User
After the user changed the expired Active Directory password, Kerberos authentication on proxy started to fail. If the same user logs into another machine with the same password everything works normally. What is going on?
Due to some unknown errors or race conditions after changing the Active Directory password it might happen that the system caches wrong credentials in the Windows Credentials Storage. All further attempts to access proxy that requires Kerberos authentication will reuse wrong credentials resulting into Access Denied message from the proxy or NTLM authentication pop-ups.
This can be confirmed by looking at the output of the klist command on the client machine. Usually, it contains the Kerberos ticket for the proxy.
C:\Users\rafael.akchurin>klist
Current LogonId is 0:0x8a6976
Cached Tickets: (8)
#0> Client: rafael.akchurin @ DILADELE.LAN
Server: HTTP/winproxy-ad.diladele.lan @ DILADELE.LAN
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a10000 -> forwardable \
renewable \
pre_authent\
name_canonicalize
Start Time: 11/10/2021 10:04:04 (local)
End Time: 11/10/2021 19:58:04 (local)
Renew Time: 11/17/2021 9:58:04 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: dc1.diladele.lan
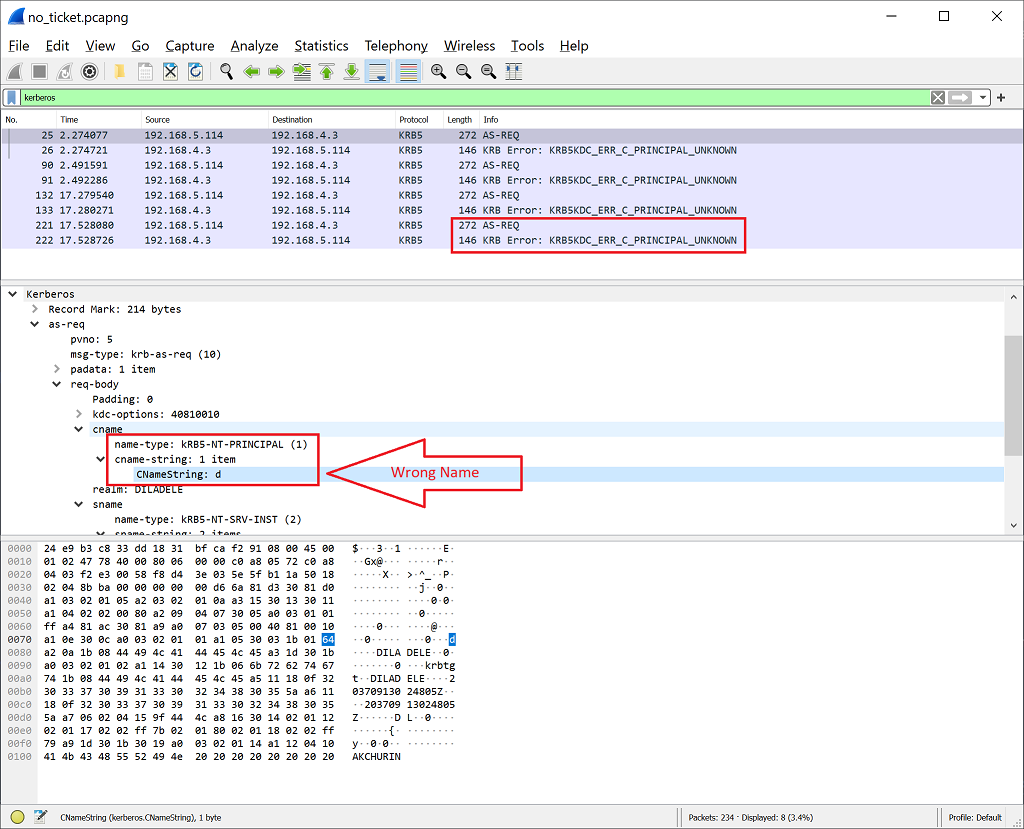
In case of wrong credentials the output of the klist will show no tickets for the proxy service. And if you do the network traffic capture at the time of the browsing - the KRB5KDC_ERR_C_PRINCIPAL_UNKNOWN error will be returned by the Kerberos server.
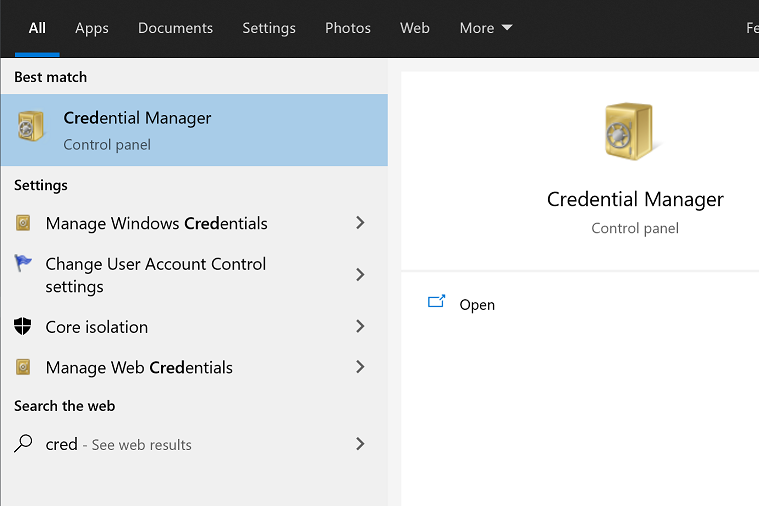
To fix this problem, open the Credentials Manager from the Start Menu as shown on the following screenshot.
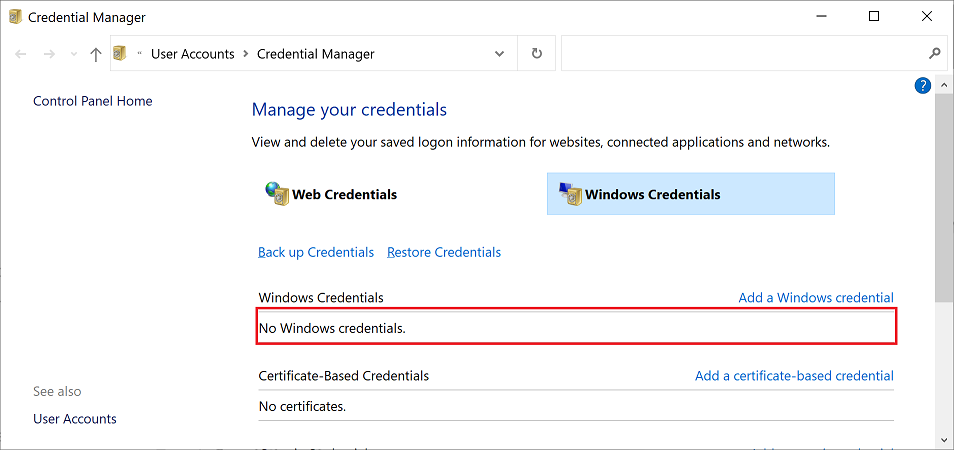
And remove all Windows credentials there.
Logoff and logon again and Kerberos Authentication error for that specific user should disappear.