Verifying Our Site-to-Site VPN Actually Works
Try Connecting to Virtual Machine
To test the site-to-site VPN we will deploy a temporary virtual machine in our resource group and try to connect to it from our on-premises network. The machine to deploy will be Windows Server 2019 Datacenter - the same image that we are going to use for all our proxy tutorials.
Specify the following parameters for deployment.
| Setting Name | Value |
|---|---|
| Virtual Machine Name | vpn-test-vm |
| Virtual Network | vnet-azure-proxy |
| Subnet | default (10.2.0.0/24) |
| Public IP | None |
| NIC network security group | None |
Wait a couple of minutes and make sure the newly created virtual machine only has private IP address from our default subnet.
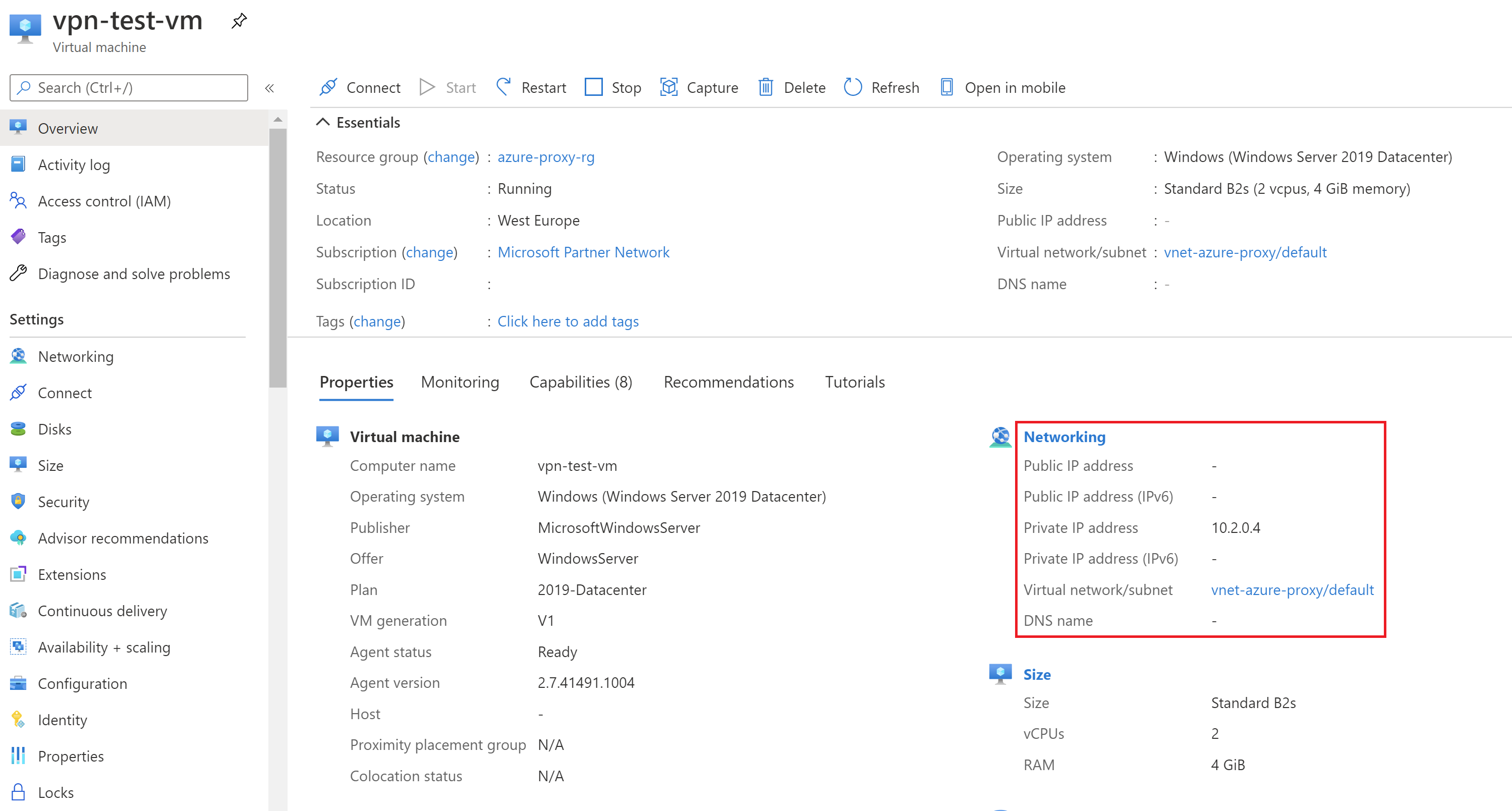
Now from your workstation on-premises try to establish the RDP connection to private IP address 10.2.0.4. Cisco ASA shall automatically establish the site-to-site VPN connection and successfully direct traffic flow to the Azure subnet through.
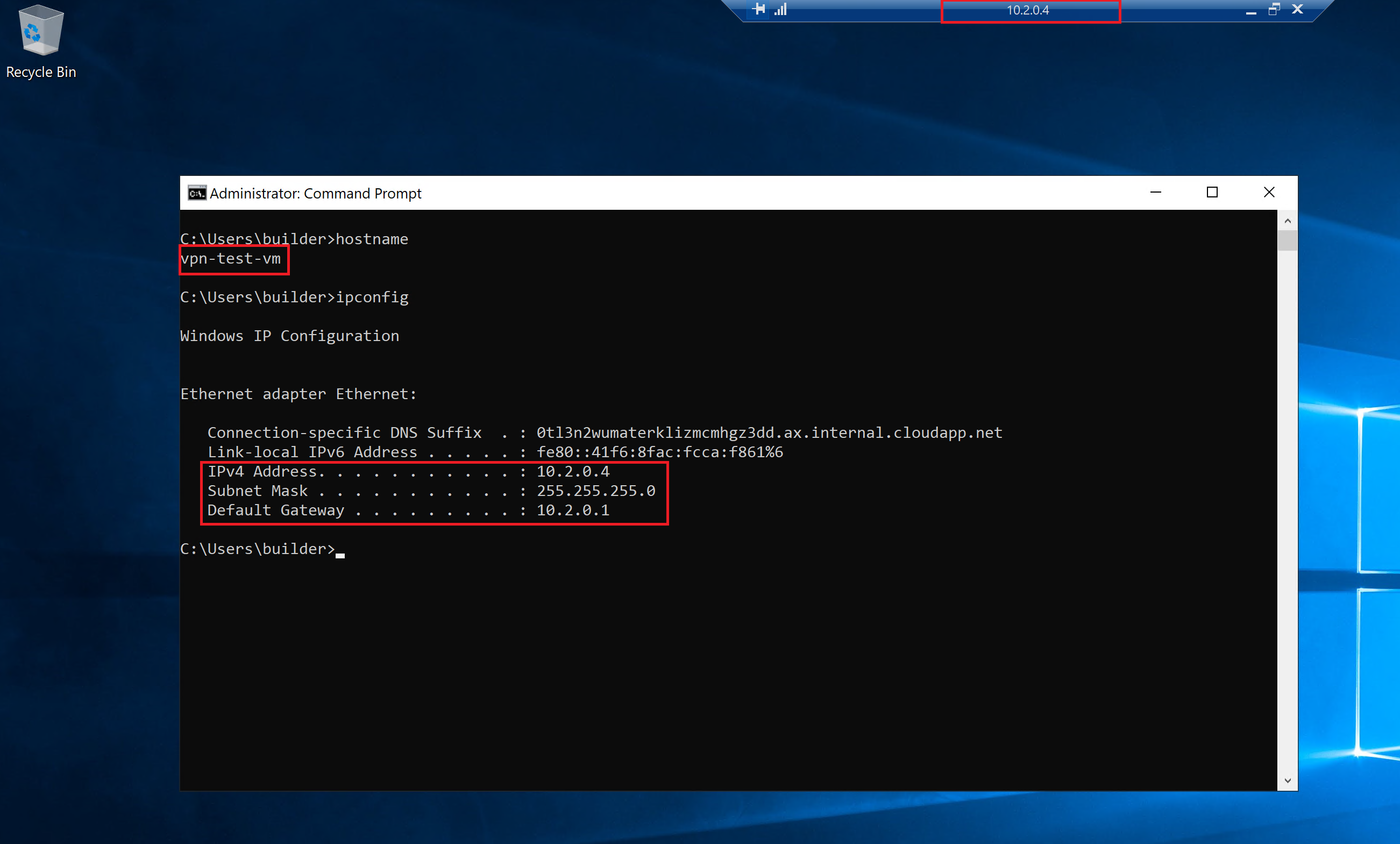
Good our cloud networking lab is up and running. We are ready to start deploying our proxies in the cloud.
Possible Errors
Configuring Cisco ASA is a lot of manual typing so a lot of things may (and will) go wrong. To test if site-to-site VPN indeed works see the output of the show cry isa command. It should indicate the active site-to-site tunnel.
ciscoasa# show cry isa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 207.46.13.105
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
Here we see the state as MM_ACTIVE so everything is fine.