Import Third-Party Certificate for Secure Proxy
As secure proxy certificate is actually a normal web site certificate, we can also purchase it or get one for free from any third-party provider. For example, it is possible to purchase the certificate from a commercial certificate provider like ssls.com or get one for free from LetsEncrypt.
It is even possible to generate your own certificate using OpenSSL and the following commands (note we added some line breaks for better readability). Do not forget to change the proxy.example.lan to your actual proxy fully qualified domain name.
$ openssl req -x509 -nodes -days 1825 -newkey rsa:2048 \
-keyout secure_proxy.key -out secure_proxy.crt \
-subj "/C=NL/ST=Noord-Holland/O=Example Ltd./OU=IT/CN=proxy.example.lan"
$ cat secure_proxy.key secure_proxy.cert > secure_proxy.pem
After you have the certificate you would need to import it into Admin UI. So open the Proxy Settings menu in Admin UI / Web Filtering Proxy section and click on the Proxy Settings node as indicated on the following screenshots.

The certificate must be encoded as PEM and must contain both private key and the corresponding certificate in one file. To import the certificate into Admin UI, click Import button and navigate to your certificate as shown on the following screenshot.
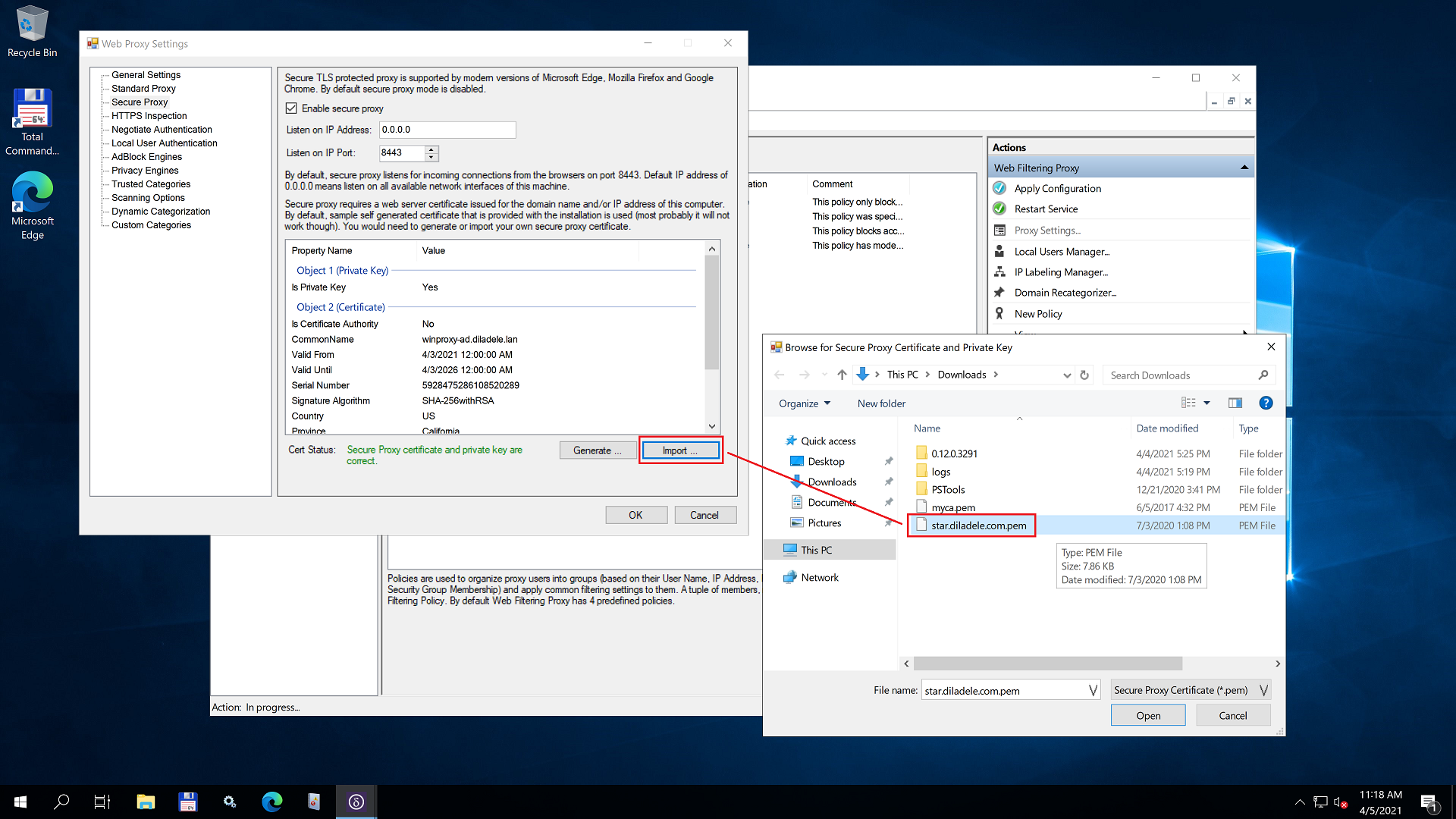
For example, here for the illustration we are selecting our existing wildcard certificate for any host in diladele.com domain to protect access to our public proxy.diladele.com deployed in the cloud. The wildcard certificate was purchased from ssls.com.
Click the Open button in the file selection dialog and the contents of the selected certificate will be stored in the C:\ProgramData\Diladele\WebProxy\N.N\etc\secure_proxy.pem file. Properties of the certificate will be displayed in the Admin UI.
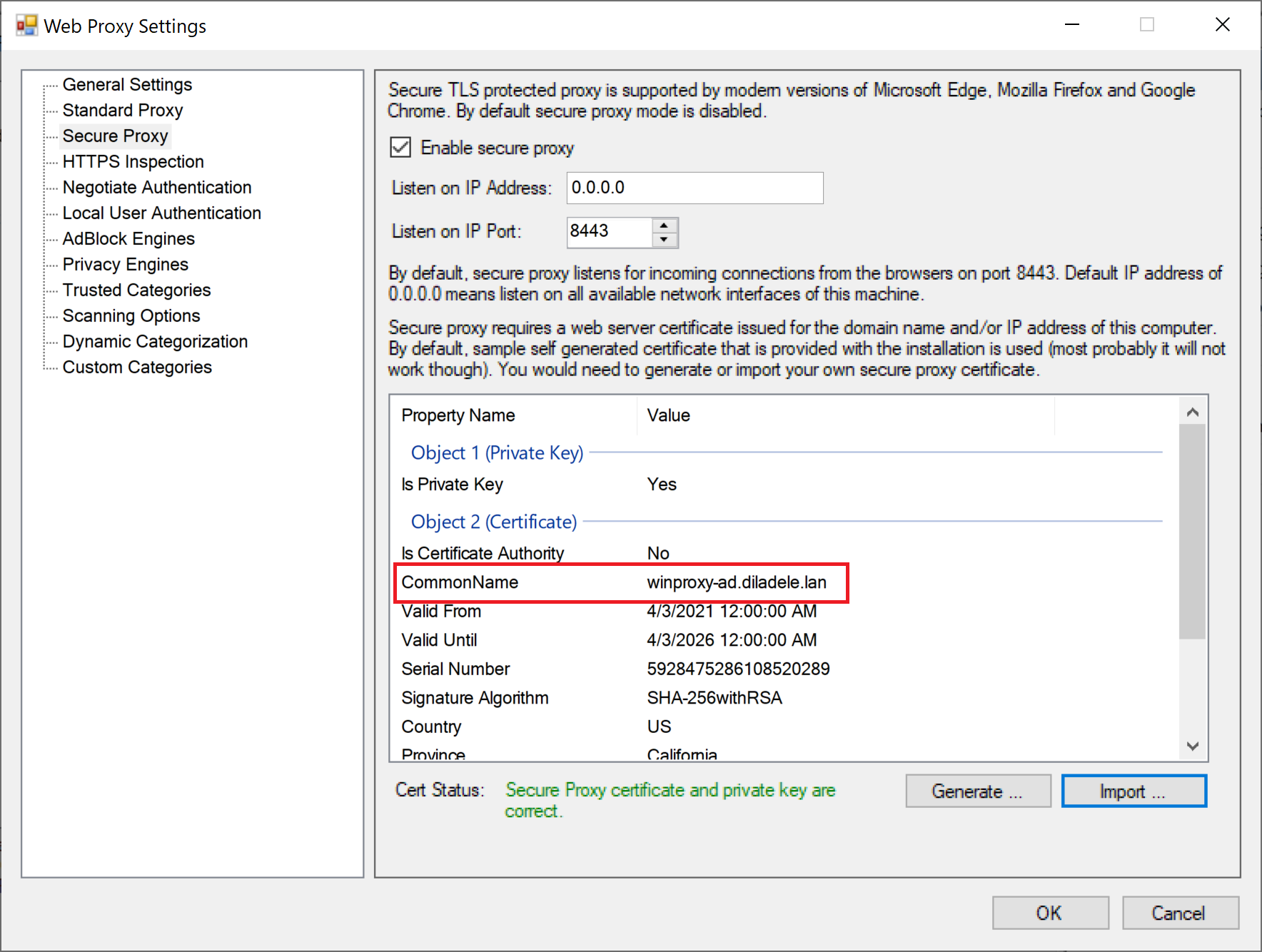
It is very important to verify that the Common Name of the imported certificate matches the fully qualified domain name of the machine where Web Filtering Proxy is deployed. Wrong common name will prevent the browser from connecting to secure proxy. Note, if you generated the secure proxy certificate using Admin UI all properties of the certificate should be correct.
Do not forget to restart the Web Filtering Proxy service in order for the changes to be applied.