Restricting Access to Specific Tenants in Microsoft Azure AD / Entra
Important
Apps and Restrictions rules can only be applied when your proxy is set to perform HTTPS decryption.
The application is able to restrict access to cloud applications belonging to specific Tenants in Microsoft Azure. To better understand why this might be very important consider reading this Microsoft article.
It is possible to enforce two variants of Tenant Restrictions:
- V1 restrictions are supported as explained in this Microsoft Help article.
- V2 (Preview) restrictions are supported as explained in this Microsoft Help article.
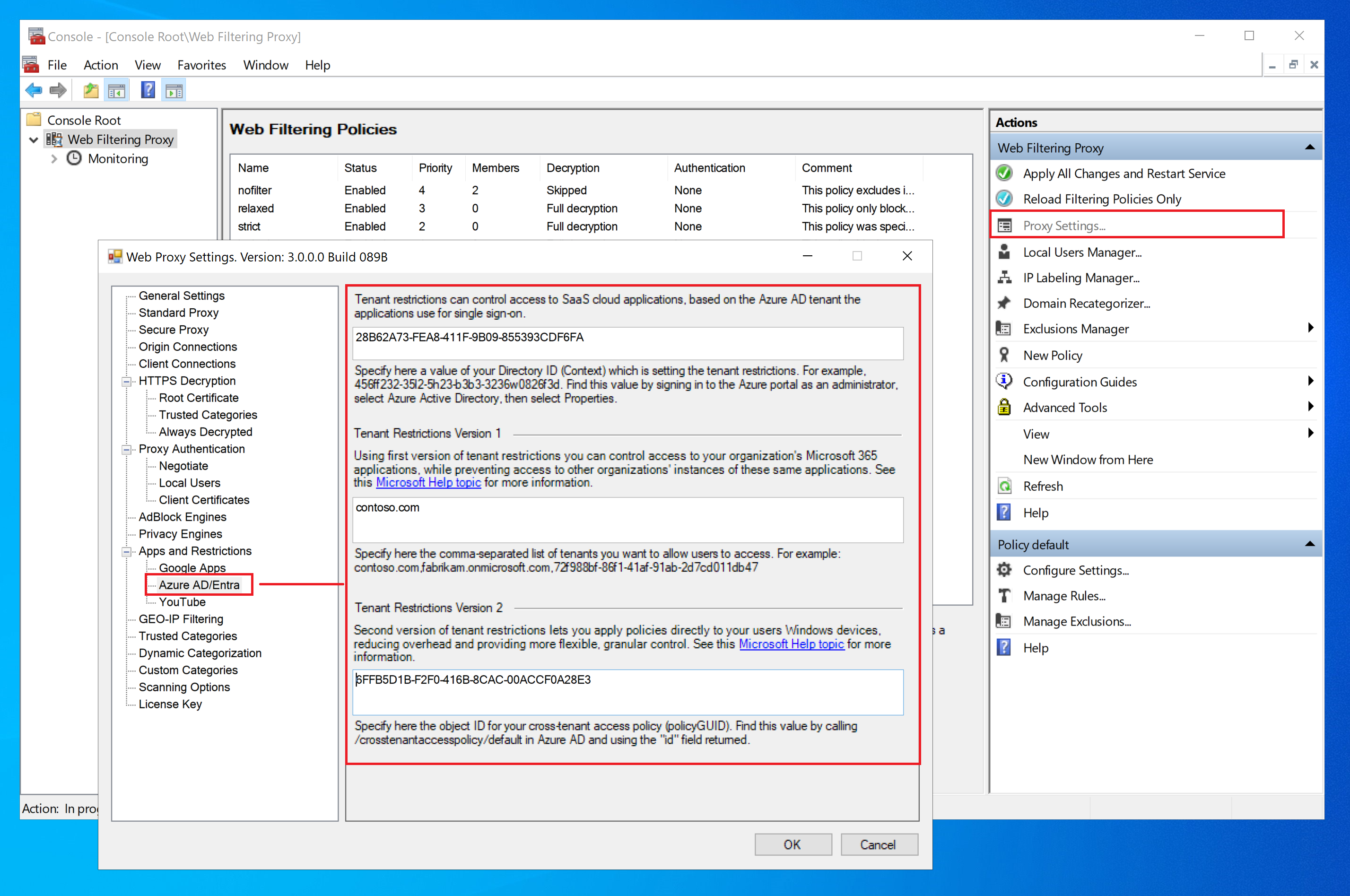
To configure this functionality, first provide the Directory ID (Context), tenant names or Policy GUIDs info in Proxy Settings / Apps and Restrictions / Azure AD (Entra) as shown on the following screenshot.
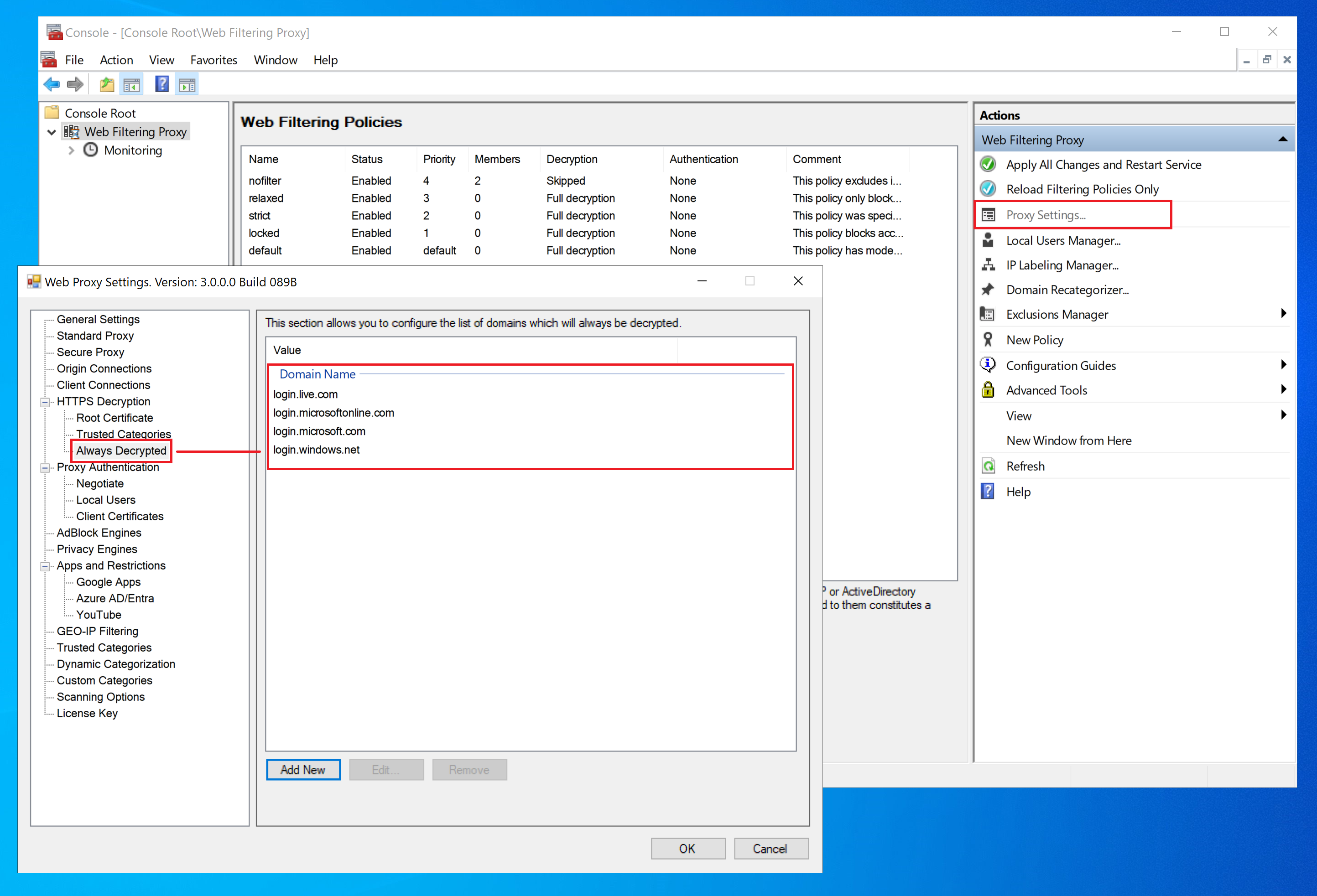
Then add the following domain names to Always Decrypted Domains in Proxy Settings
login.live.com
login.microsoftonline.com
login.microsoft.com
login.windows.net
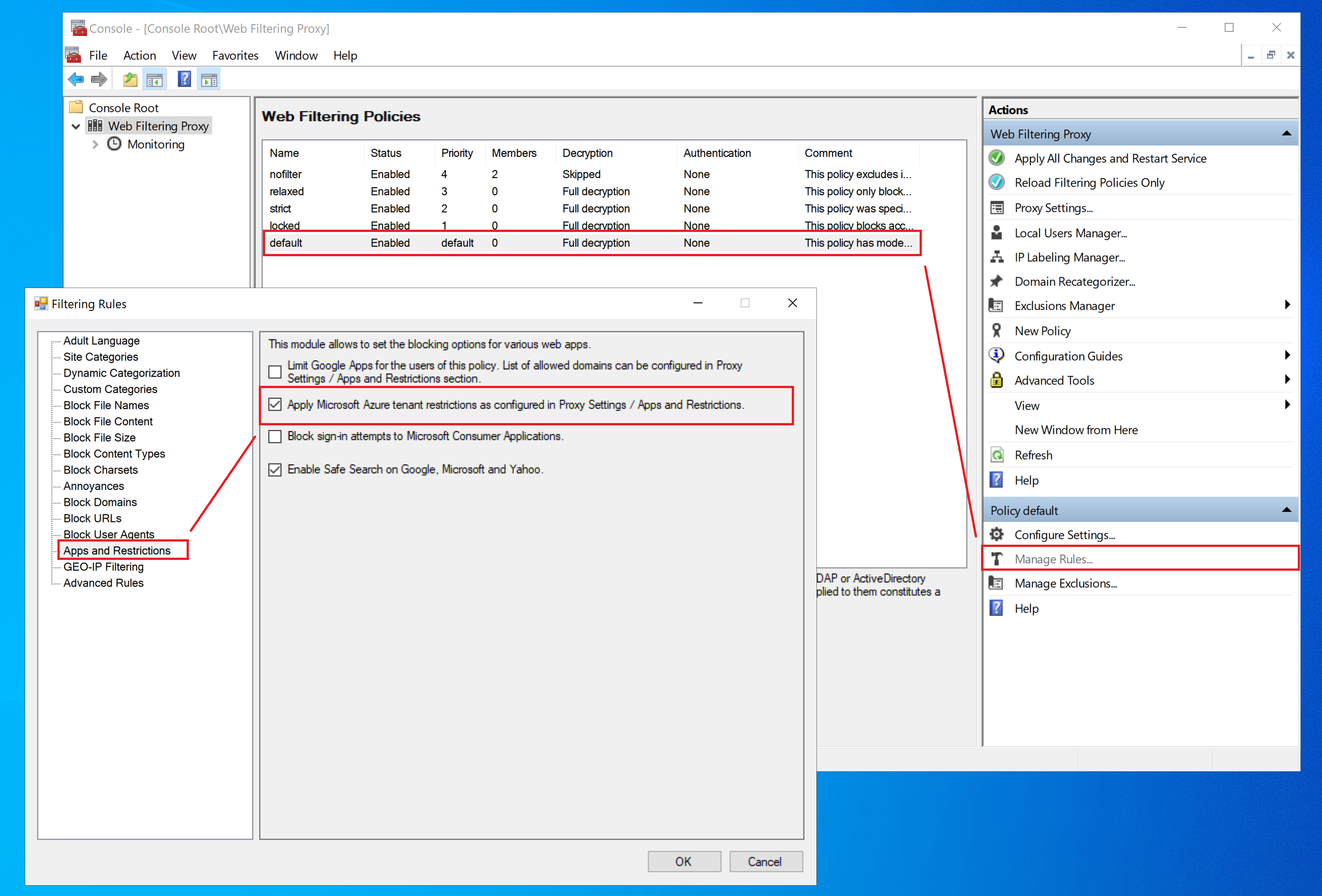
And finally enforce tenant restrictions for specific policy.
When users will try to login to the cloud application using different tenant than specified by the administrator - the access will be restricted.