Decryption of HTTPS Traffic
Web Filtering Proxy is capable of decrypting and inspecting of HTTPS connections (assuming browsers are trusting the proxy of course).
Decrypting Flow
The following describes what happens when a user needs to navigate to a web page that is to be HTTPS decrypted and inspected.
- User types a domain name in the browser address bar.
- Browser sends the request to proxy server, asking it to establish a secure CONNECT tunnel to remote origin server.
- Proxy establishes a secure HTTPS connection to the remote server and retrieves the server certificate.
- Proxy generates a new certificate the remote server, imitating all properties of the original certificate and signs this imitated certificate using its own Root CA certificate.
- Proxy sends that imitated certificate to the browser along with the message that the connection is successfully established.
- Browser accepts the imitated certificate, validates it and (because browser trusts the proxy) sends the request through the connection to the proxy.
- Proxy receives the request, filters it and passes it to origin server.
- When origin server replies with response, proxy filters that response and forwards it to the browser.
Taking a look at this flow of events we understand that we need at least two things to configure for the successful HTTPS inspection.
- Proxy needs to be configured with a certificate that can act as trusted Root CA.
- Browser needs to be set to trust that Root CA
The following pages will go into more details on these two subjects.
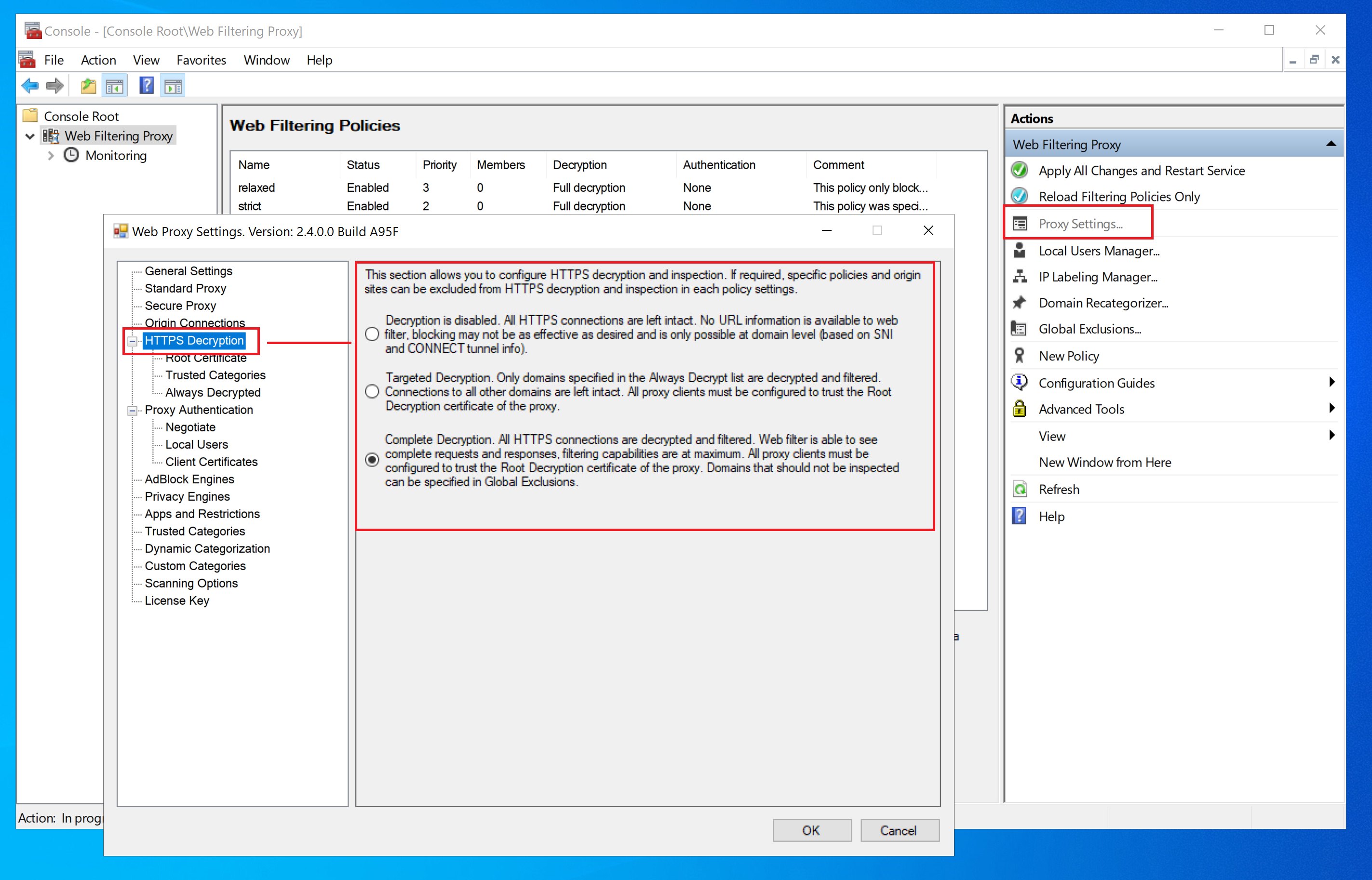
Decryption Modes
Web Filtering Proxy can function in three distinct modes regarding HTTPS decryption. These are described in the following table.
| Mode | Description |
|---|---|
| No Decryption | Default mode. No HTTPS decryption and deep content filtering is performed. Web filtering may not be very effective because proxy does not have access to actual textual contents of HTML pages being transferred. Only web filtering by domain names being connected to is active. |
| Targeted Decryption | In this mode only sites specified by the administrator are decrypted and filtered. All other sites remain intact. Web filtering by domain names being connected to is also active. |
| Complete Decryption | All HTTPS connections are decrypted and filtered. The administrator may indicate some categories of the domains that are excluded from decryption automatically. For example, connections to financial and government institutions, medicine and health organizations, etc. |
To select the active mode, navigate to Proxy Settings / HTTPS Decryption and choose the desired mode as shown on the following screenshot.