Enabling the HTTPS Decryption and Inspection
After you have generated or imported the Root CA certificate and private key and marked it as Trusted Root CA in the certificate store of the operating system there is one more step that needs to be done.
Select Decryption Mode
To enable HTTPS decryption, choose either Targeted Decryption or Complete Decryption mode in Proxy Settings / HTTPS Decryption page.
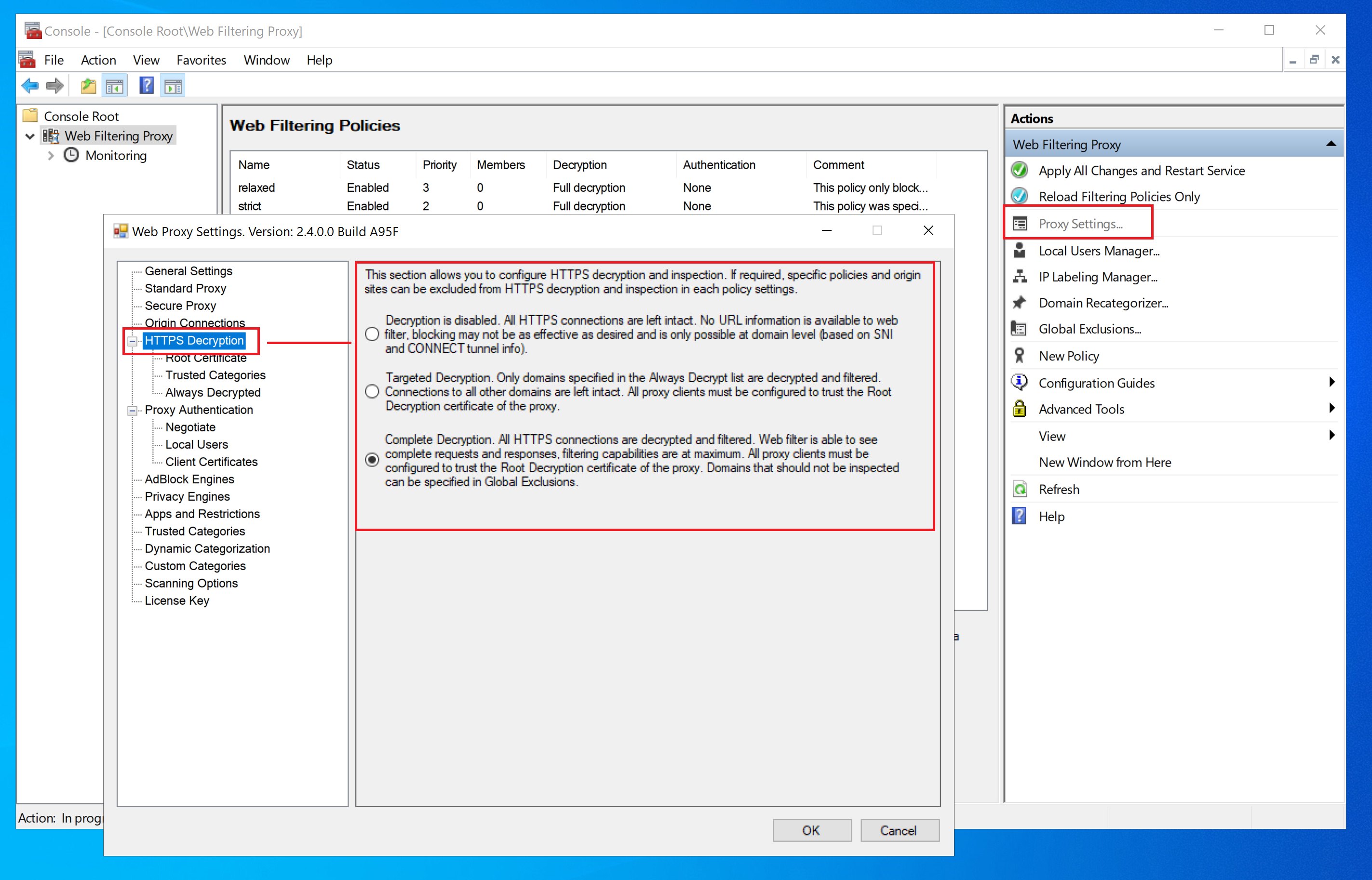
In Targeted Decryption mode only domains which are part of Always Decrypted list are decrypted. To manage this list, click on HTTPS Decryption / Always Decrypted node.

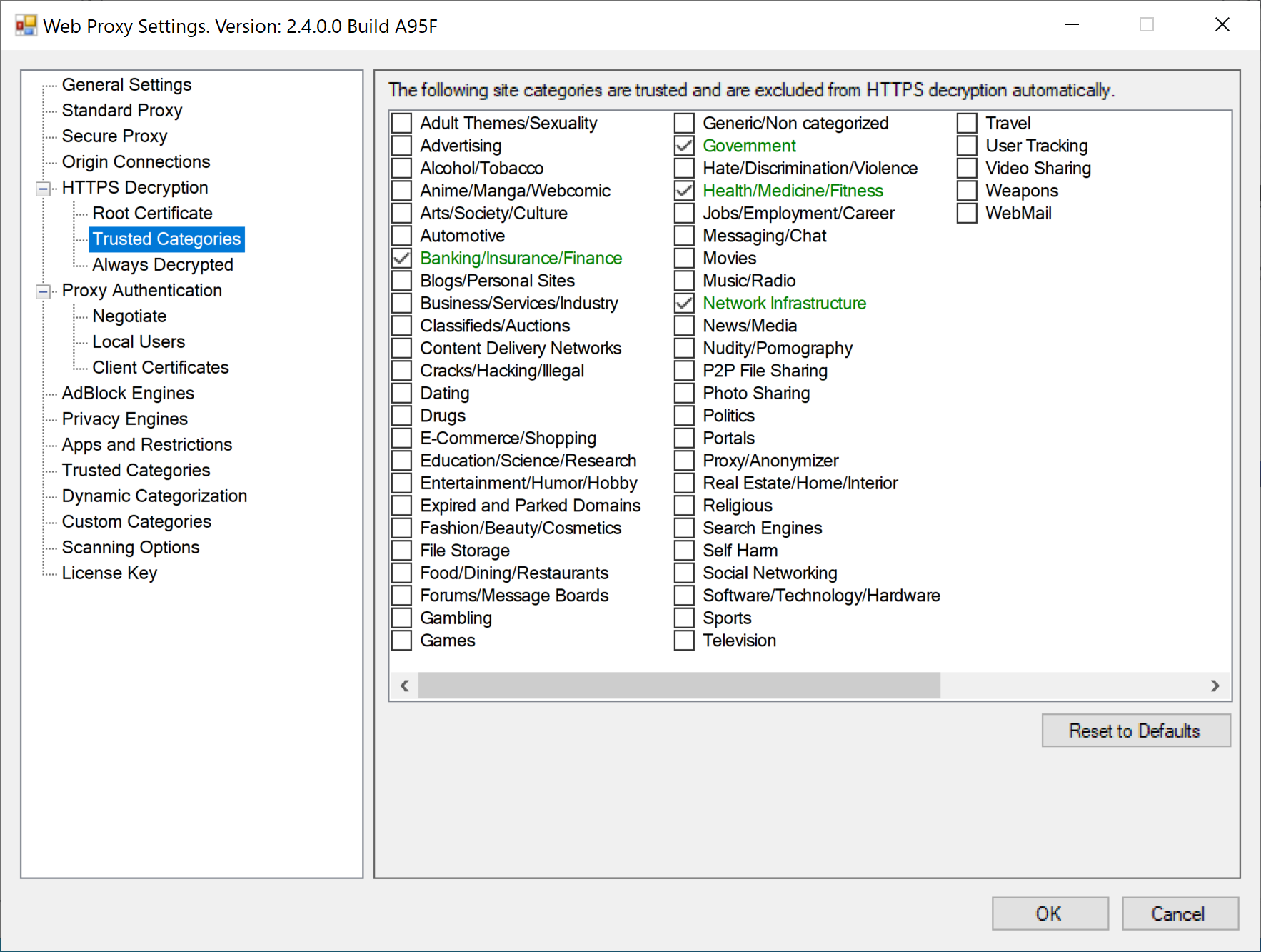
In Complete Decryption mode all domains are decrypted. The application allows to automatically bypass decryption on highly trusted domains - for example, privacy sensitive sites, government, financial institutions, health and personal sites.
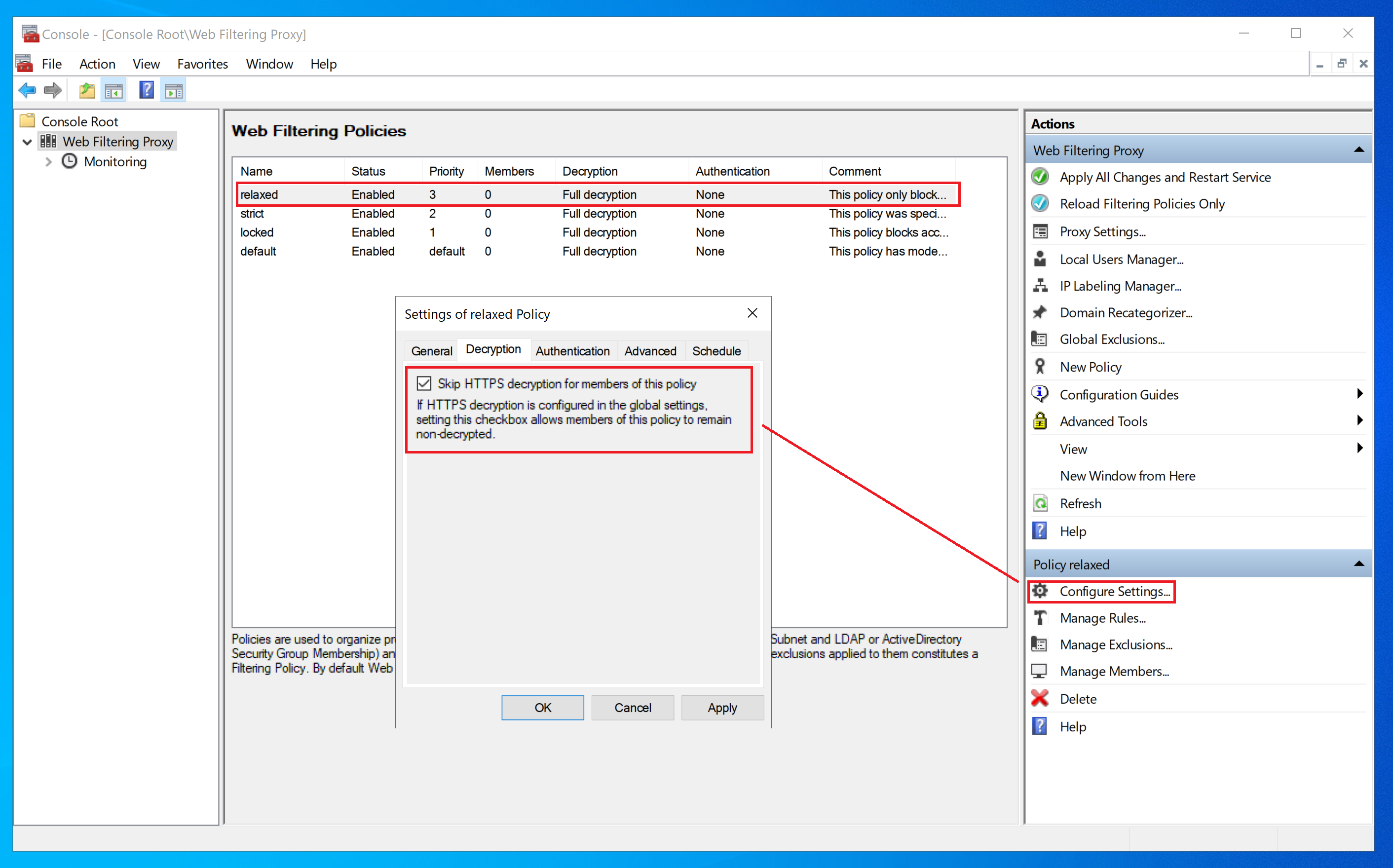
Adjust Decryption per Policy
Web Filtering Proxy can also adjust HTTPS decryption per policy. To skip HTTPS decryption for a given filtering policy, open policy settings, select the Decryption tab and set the checkbox as shown on the following screenshot.
Verify HTTPS Decryption Works
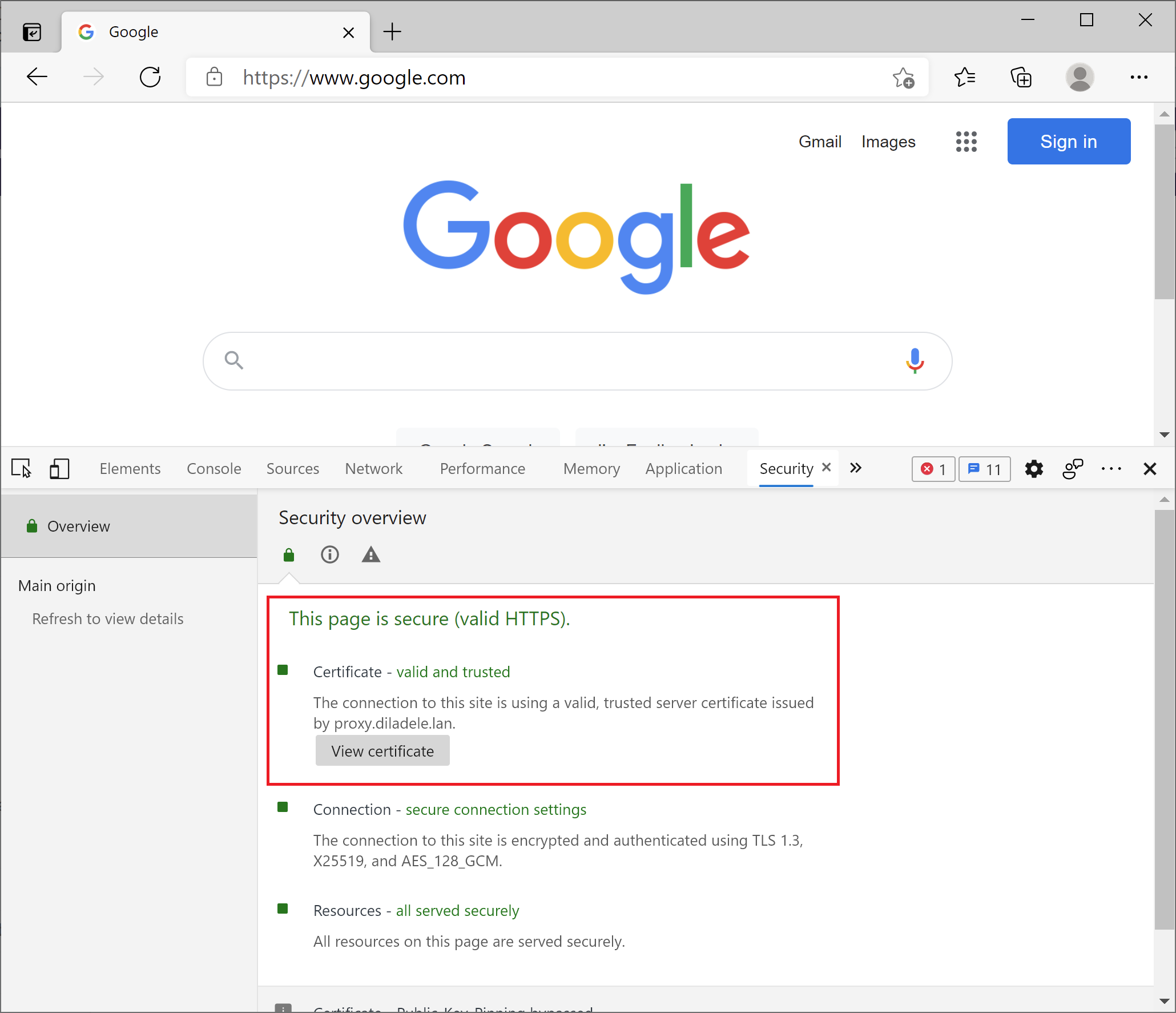
After HTTPS decryption was enabled and browser set to trust the Root CA certificate of the proxy browsing shall work normally and clicking on the certificate lock in the browser shall show the notification message. Note that you need to see the name of your Root CA.
For example, this screenshot presents the decrypted and inspected HTTPS page in Mozilla Firefox.
This screenshot presents the decrypted and inspected HTTPS page in Microsoft Edge (network tools tab is open).
The Web Filtering Proxy is now fully configured to inspect the decrypted traffic and perform web filtering.