Configure Browsers to Use the Proxy
Configure the browser to use the clustered proxy by fully qualified domain name of the cluster. This is important for proxy authentication we are going to configure on the next step, because transparent Negotiate/Kerberos authentication does not work when proxy is set to simple IP address.
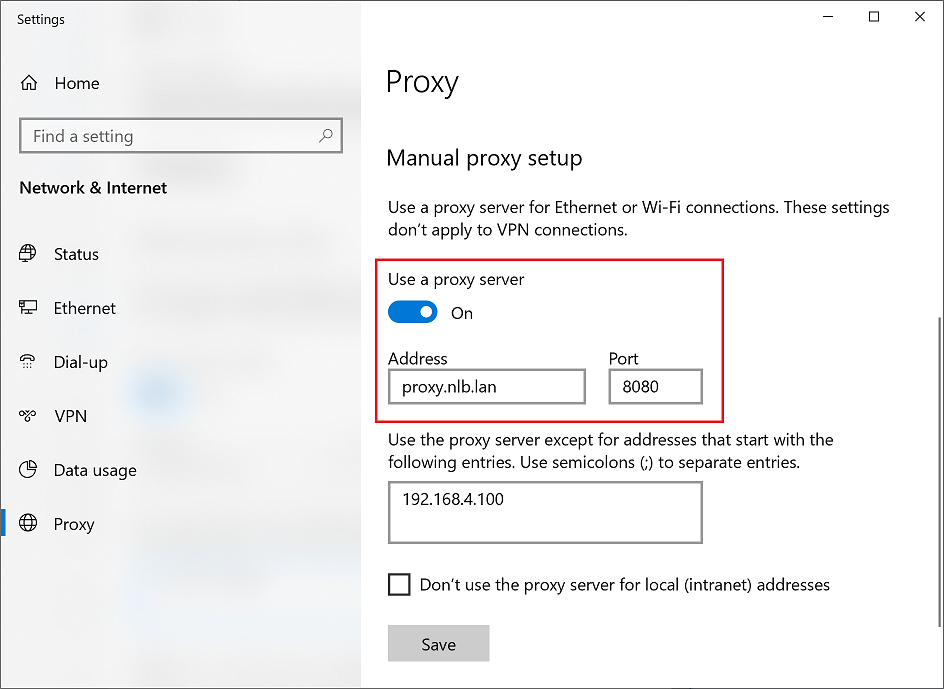
Note that there are various methods of how to configure the browser automatically, but for the purpose of this tutorial we will go with the most simple one.
Try browsing the Internet and see that Performance Counters on both proxy nodes indicate traffic is nicely flowing from the browsers.