Firewall Settings
Network Security Group
After deploying the marketplace image of Web Filtering Proxy we have a new Network Security Group that contains the following firewall rules for incoming connections.
| Rule Name | Protocol | Port | Source | Destination | Action |
|---|---|---|---|---|---|
| Plain_Proxy | TCP | 8080 | Any | Any | Allow |
| Secure_Proxy | TCP | 8443 | Any | Any | Allow |

The ports are the listening ports for standard conventional plain proxy (8080) for this tutorial and 8443 for secure proxy (see next tutorial). Default rule for RDP access has also been added by Microsoft.
Go ahead and remove the Secure_Proxy firewall rule, from now on our proxy will only be accessible over port 8080.
We now need to allow connections to this ports from our public IP address only. All other connections shall be denied. We assume from now on you know the public IP address (range, subnet) that was assigned to you by your ISP provider. If not, seach on Google for what is my public ip.
Click on each incoming rule and provide the IP address or address range which are allowed to connect to our plain proxy port 8080 and RDP. Note this will limit the incoming connections to your proxy to your public IP address only. If you happen to roam through networks (like using 4G for accessing the proxy) these firewall rules will interfere with normal operations. In this case a secure proxy tutorial should be used instead.
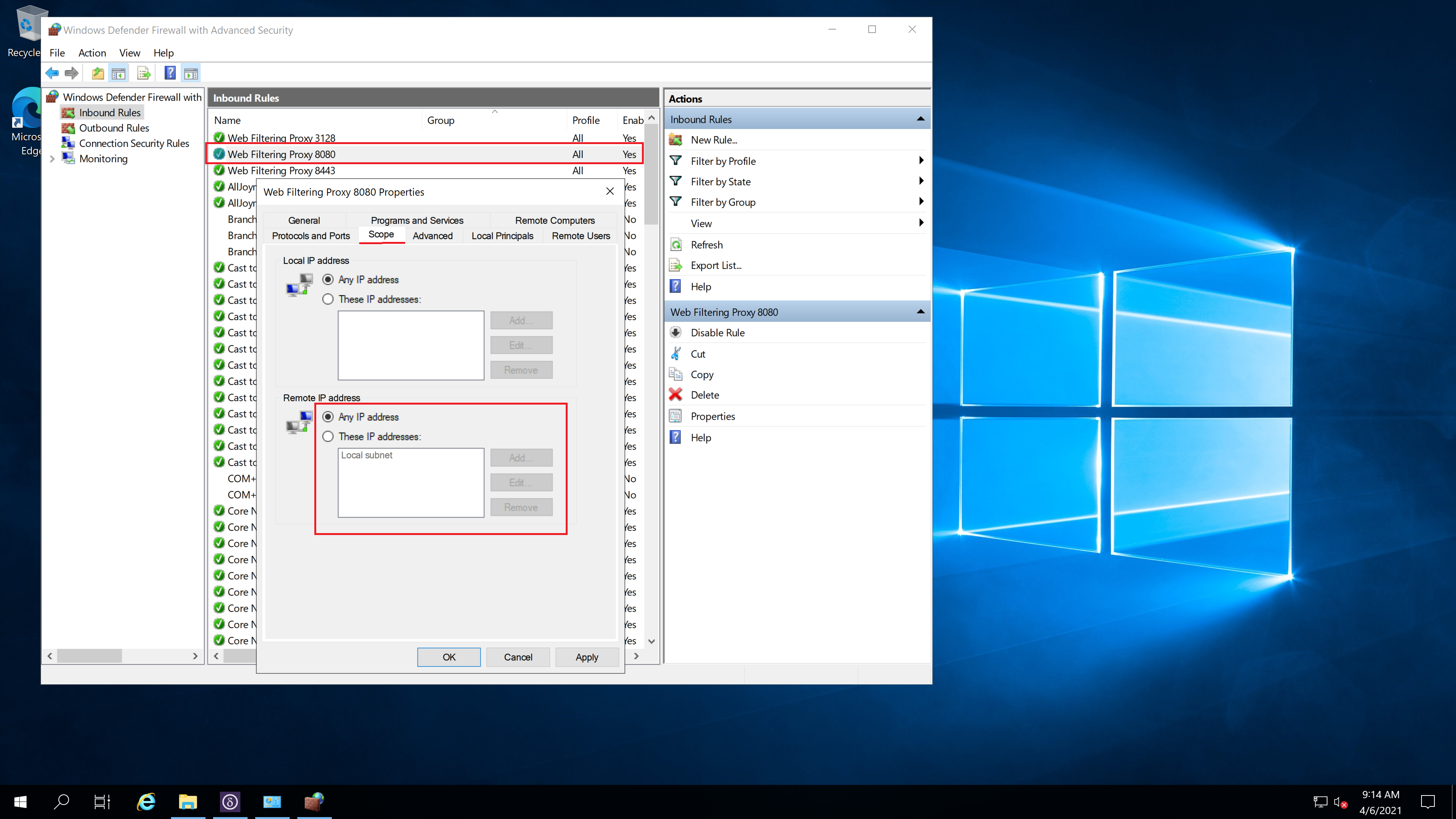
Windows Firewall
The local built in Microsoft Windows Firewall on the virtual machine also needs to be adjusted. By default when Web Filtering Proxy is installed it adds several firewall rules that allow incoming connections from the private LAN scope only. As we are deploying the standard proxy in the cloud we also need to allow connections to ports 8080 from any host as shown on the following screenshot.