Client Certificates
Next step is to generate the client certificate for each of the connecting client.
For the purposes of this tutorial we will re-use decryption certificate as the signing authority. Note for the decryption to work the client must trust the proxy anyway so it makes sense to also reuse this trust for client authentication. In real production the client certificate may be generated by your Microsoft PKI infrastructure for example.
Unfortunately the Admin UI has no ways to generate the client cert so we will use openssl command on Linux to do that for this tutorial. Note, most probably generation of client certificates will be done automatically in production so these commands are only here to illustrate the general idea.
# create the client private key
openssl genrsa -des3 -out user.key 4096
# create a Certificate Signing Request (CSR), when answering
# questions set the CommonName and E-Mail to the value you
# need (like user name); this value will then be used in
# proxy authentication (here we set it to john.rambo@example.lan)
openssl req -new -key user.key -out user.csr
The sample output is shown below.
root@node12:~/nebraska# openssl req -new -key user.key -out user.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Nebraska
Locality Name (eg, city) []:Lincoln
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Example LLC.
Organizational Unit Name (eg, section) []:IT
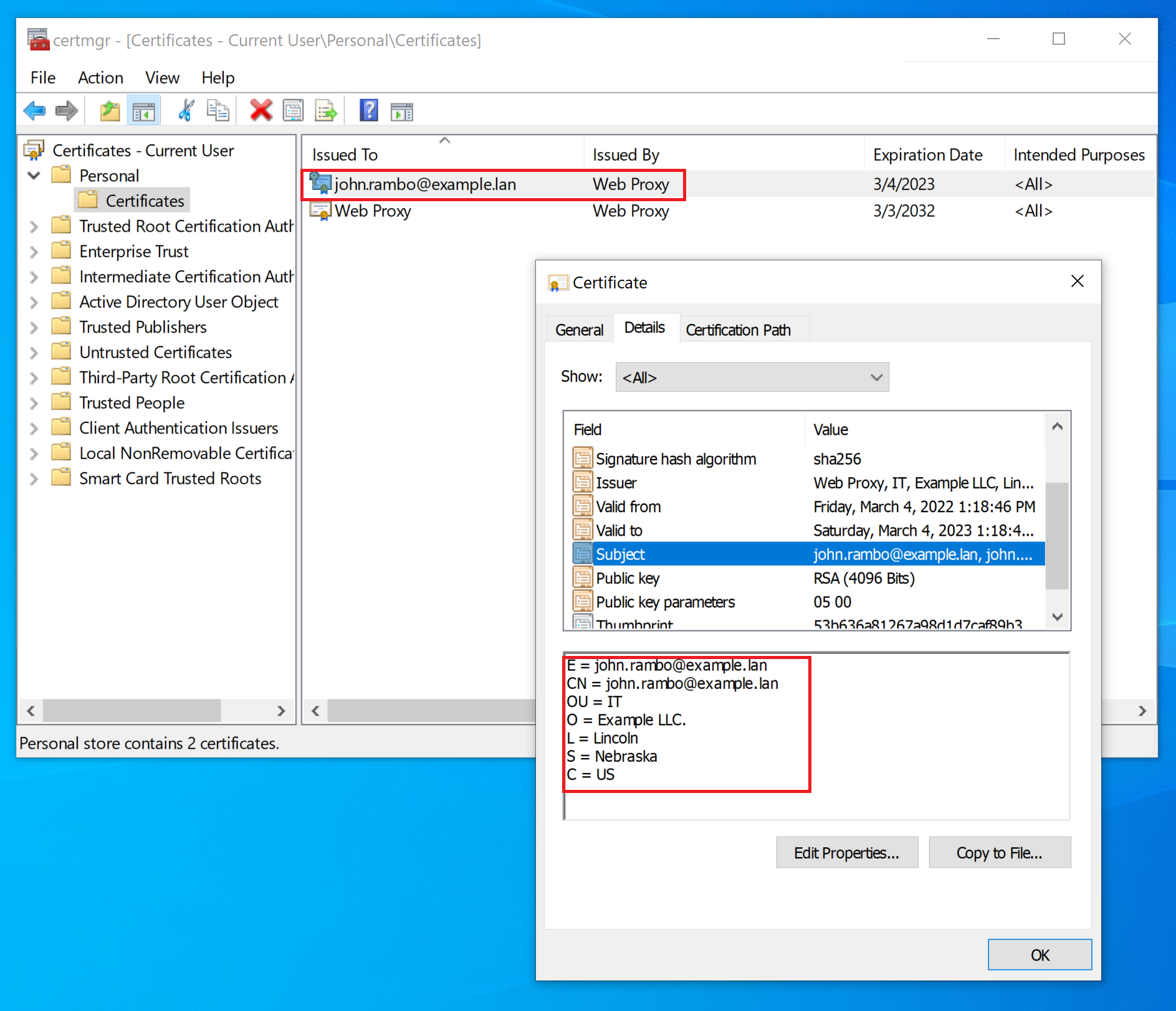
Common Name (e.g. server FQDN or YOUR name) []:john.rambo@example.lan
Email Address []:john.rambo@example.lan
We will then need to sign this certificate request with our decryption certificate. Be sure to increment the serial number with each client certificate generated.
openssl x509 -req -days 365 \
-in user.csr -CA myca.pem -CAkey myca.pem \
-set_serial 01 -out user.crt
Finally we need to combine the user private key and certificate into one file, to later install in on Microsoft Windows machine.
openssl pkcs12 -export -out user.pfx \
-inkey user.key -in user.crt \
-certfile myca.pem
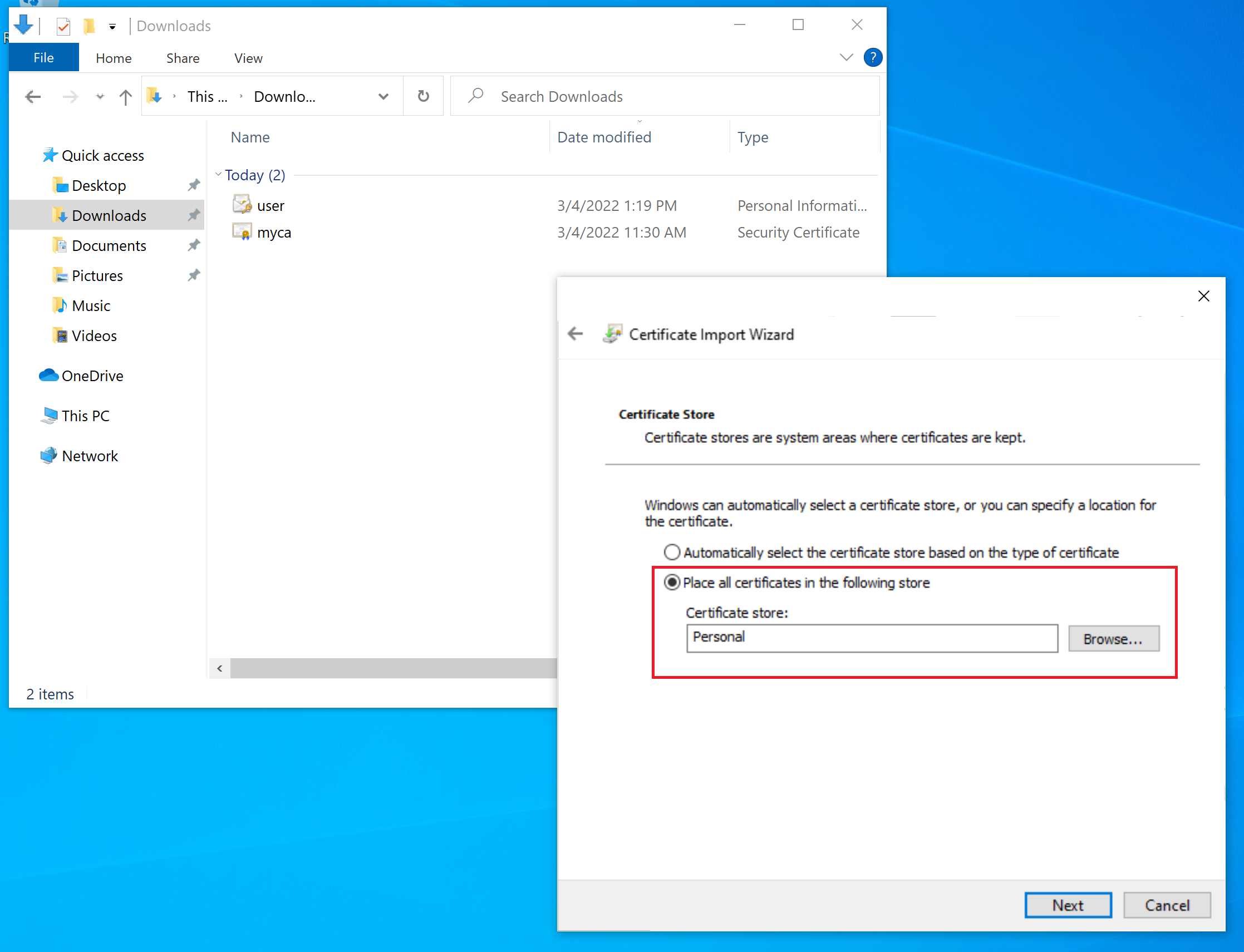
Copy the user.pfx to the user machine (note each user must have different certificate) and double click it to install. The following screenshots show the installation process.
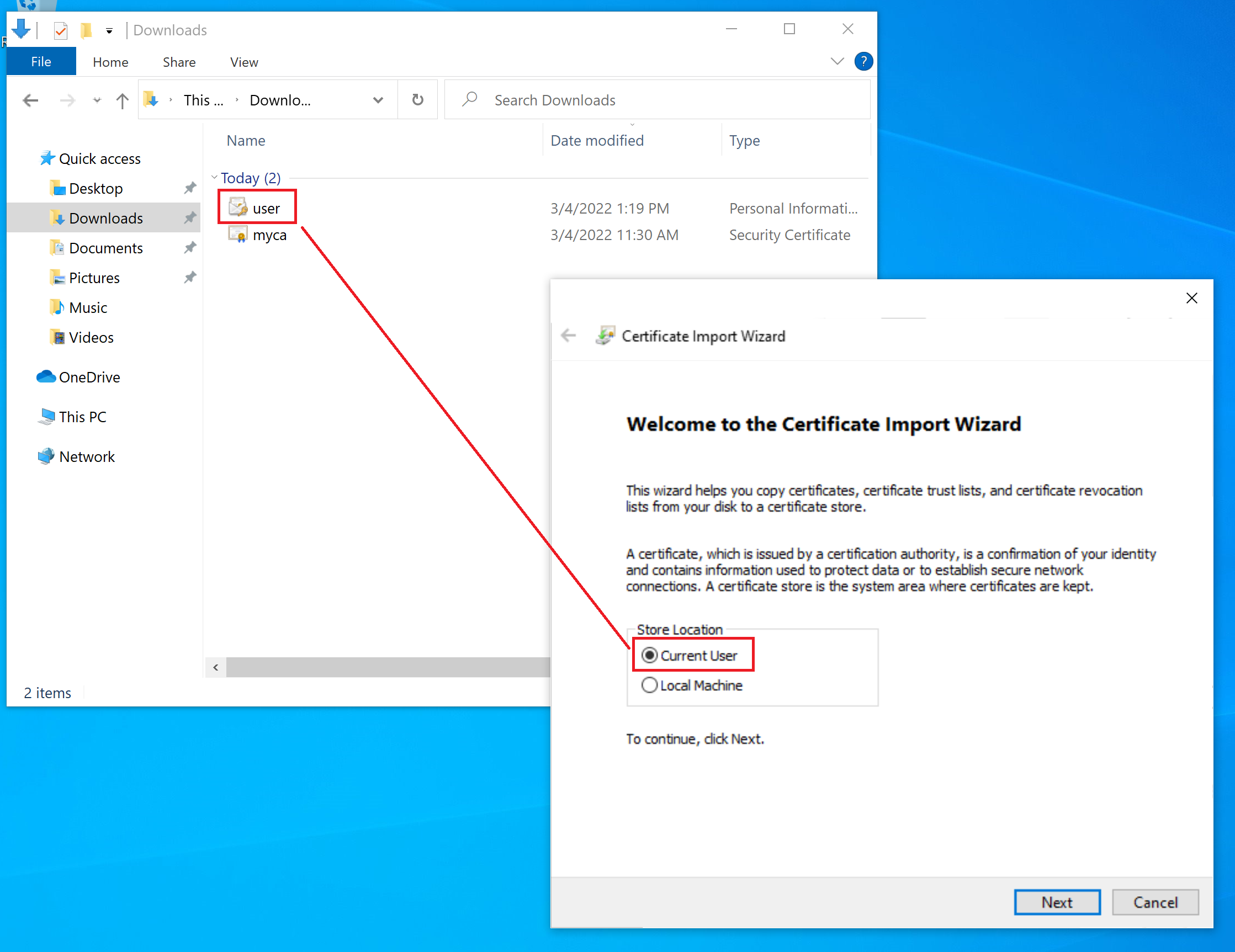
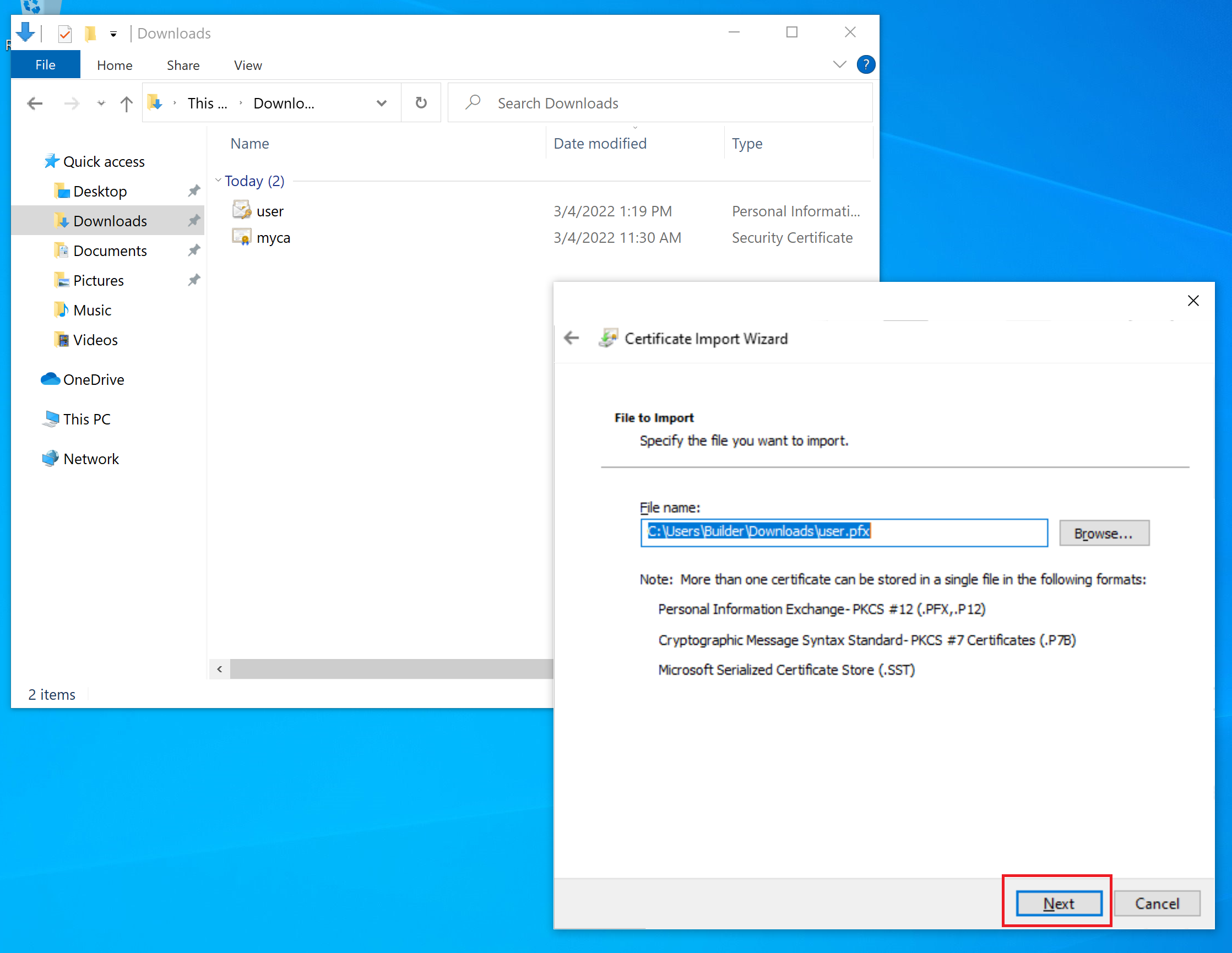
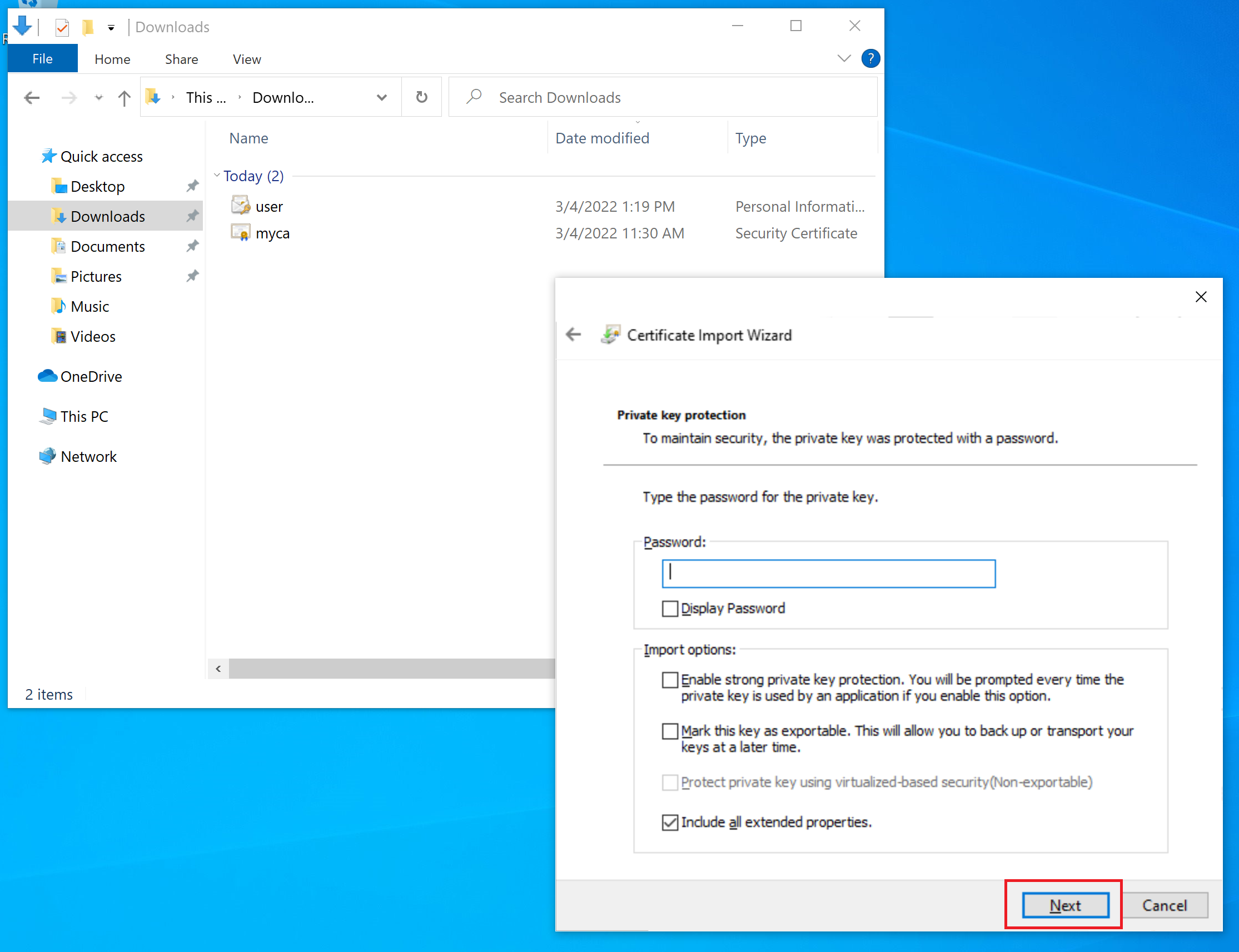
Put the certificate into Personal Store.
Verify the certificate was installed correctly.