Policy Selection Algorithm
Administrator can configure different web filtering policies for different proxy clients. The following steps describe how exactly the application selects the filtering policy for a connecting client.
- Upon start, the application reads the list of policies from the configuration and sorts it according to the priority (from high to low).
- Let's now assume that a user types the https://www.example.com/ URL in the browser address bar and presses Enter.
- Browser opens a new TCP connection to the proxy.
- Proxy accepts the TCP connection and extracts the IP address of the connected client.
- Looping through the priority-sorted list of policies, the application selects the policy based on IP address of the connected client. Usually this results into default policy being selected.
- If proxy is set to not require authentication or advanced settings of a selected policy indicate to skip authentication - policy selection algorithm is considered complete and web filtering module starts processing and allows or denies the request/response.
- Otherwise, the authentication process is initiated; if authentication fails for some reason (like say the connecting client does not know the valid password) - connection is terminated. Algorithm is complete.
- When the client successfully authenticates to the proxy - the next policy selection round is started - but this time not only using client IP address but also client user name.
- After the policy is selected second time, web filtering module starts processing and allows or denies the request/response.
Thus, when proxy authentication is enabled the overall policy selection algorithm becomes two-phased. This complexity leads to some non-obvious conclusion.
Recommendation
When you enable proxy authentication mode - be sure to always clear the Skip Authentication checkbox on the advanced settings of the default policy. This will ensure the proxy authentication works as you would expect.
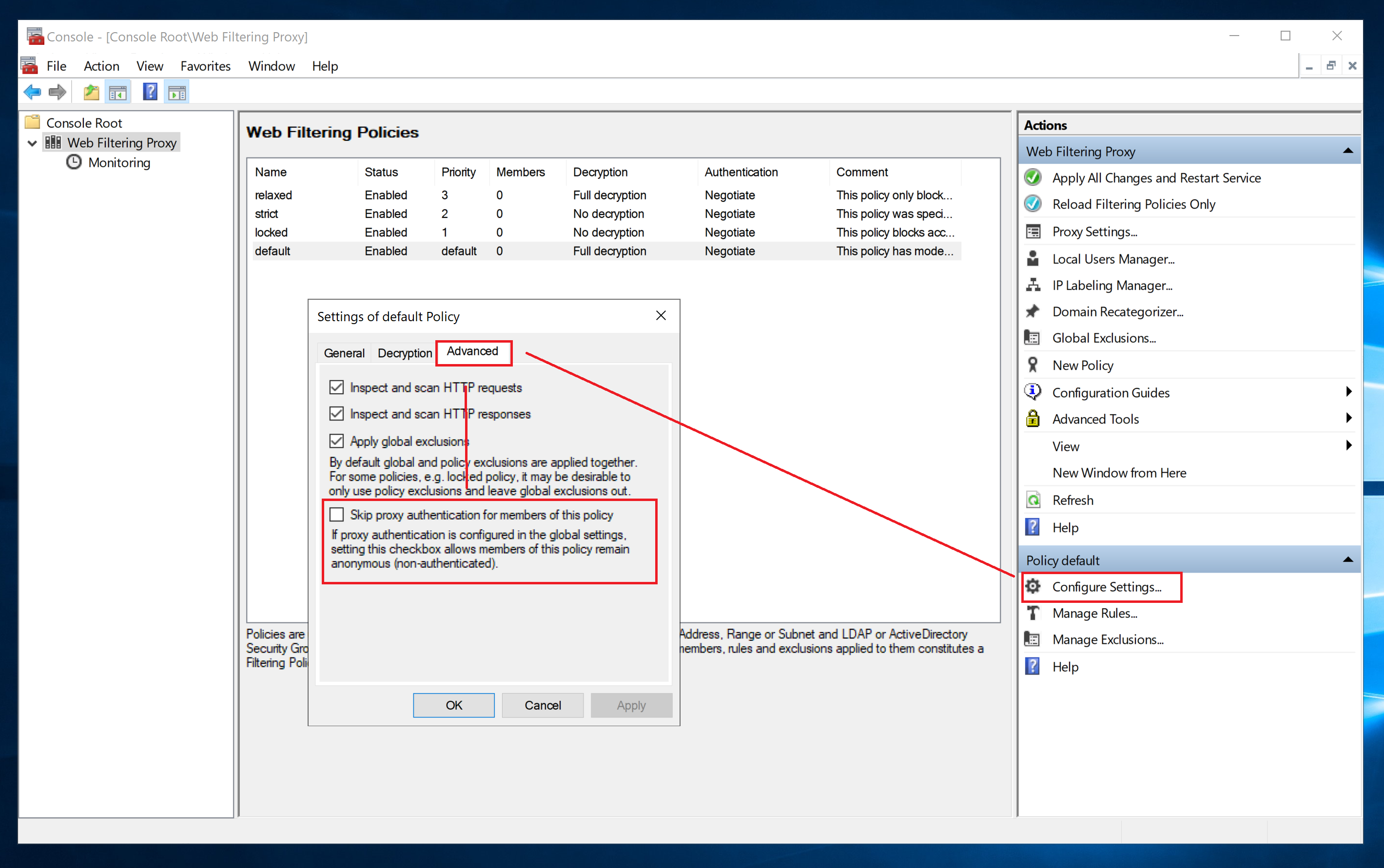
Also note that the policy selection algorithm stops after the first matching policy is found. No other policies are checked after successful match. This is so by design and keeps the system simple and predictable.